Cybersecurity Solutions
We specialize in building advanced security infrastructure to protect digital assets, whether it’s securing enterprise networks, creating real-time threat detection platforms, or developing zero-trust security solutions for organizations of any size.
Contact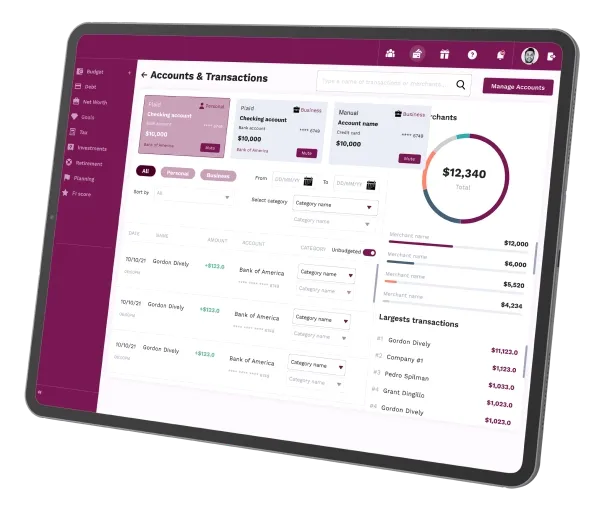
Strategic Threat Defense
Safeguard your organization with advanced threat detection and response solutions. We build proactive systems that identify vulnerabilities, prevent breaches, and adapt to the ever-changing cyber threat landscape.
Tailored Protection for Your Infrastructure
Every organization has unique vulnerabilities. Our cybersecurity experts design custom defense architectures that align with your operational needs—whether it’s endpoint protection, identity access management, or secure cloud integration.

Securing Startups with Scalable Defense
Launch your startup with confidence by embedding security from day one. Our cybersecurity frameworks are designed to evolve with your business, keeping your data, apps, and users protected as you grow.

Modernizing Enterprise Cybersecurity
Bring your security strategy into the future with next-gen technologies. From AI-driven threat monitoring to real-time incident response, we empower enterprises to stay ahead of cyber risks and maintain digital trust.

 What we offers
What we offersSecure Your Business with Cybersecurity Solutions
By doing a financial analysis of these statements, you can see
whether you have enough working capital.
Threat Intelligence & Detection
Stay ahead of cyber threats with proactive monitoring, real-time detection, and advanced threat intelligence. We help you uncover vulnerabilities and respond before breaches occur.
Custom Security Architecture
We design cybersecurity solutions tailored to your organization’s structure, whether you're securing cloud systems, internal networks, or customer data pipelines. No two systems are alike — and neither are our defenses.
End-to-End Cybersecurity Strategy
From risk assessment to incident response, we provide full-lifecycle security services. Our experts guide you through every phase — securing endpoints, networks, identities, and compliance requirements.
Next-Gen Cyber Defense
Leverage AI, automation, and zero-trust frameworks to build resilient and adaptive defenses. We help you deploy cutting-edge solutions that evolve as threats do.
Scalable Security Services
Whether you're a startup or an enterprise, our cybersecurity solutions scale with your growth. We implement flexible and efficient protections that adapt to your expanding digital footprint.
Compliance-Ready Frameworks
Ensure your business meets industry-specific regulations like GDPR, HIPAA, or ISO 27001. We simplify the compliance journey with structured frameworks and continuous monitoring.
Cybersecurity Solutions Built for Resilience
We break down barriers so teams can focus on what matters – working together
to create products their customers love.
Proven Expertise in Cybersecurity
With over a decade of experience, we deliver trusted cybersecurity strategies that protect your infrastructure from evolving digital threats.
Scalable Security Frameworks
Our solutions grow with your business — from startups to enterprises — ensuring robust protection across cloud, on-premise, and hybrid environments.
Cost-Effective Risk Management
We provide affordable security services that help you reduce risk, avoid breaches, and meet compliance without compromising your budget.
High-Quality Security Engineering
Ensure privacy and security of sensitive legal data with encryption, access control, and compliance with legal data standards.
Customized Defense Strategies
Whether you're starting fresh or enhancing an existing system, we design bespoke cybersecurity plans aligned to your unique threat landscape.
Data-Driven Threat Insights
Make smarter security decisions with advanced analytics and threat intelligence that uncover vulnerabilities and help prioritize risk mitigation efforts.
 What we offers
What we offersEnd-to-End Cybersecurity Solutions
Seamless Security Integration
Integrate robust cybersecurity measures with your existing infrastructure to protect workflows, enhance user trust, and ensure secure operations without disruption.
End-to-End Risk Management
Manage your organization’s full security lifecycle — from threat analysis and solution design to implementation and compliance — all with precision and accountability.
Dedicated Security Experts
Work with a focused team of cybersecurity professionals who monitor, assess, and strengthen your security posture with undivided attention and proven expertise.

Rapid Incident Response Teams
Quickly address emerging threats with rapid-response cybersecurity specialists who ensure continuity, minimize risk, and provide full visibility during critical incidents.
FAQ
Cybersecurity software development involves designing and building custom tools and systems to protect digital assets, networks, applications, and sensitive data from threats. This includes firewalls, encryption systems, threat detection platforms, access control, and compliance automation.
Cybersecurity solutions safeguard your business from data breaches, downtime, and reputational damage. They ensure compliance with regulations, protect customer trust, and enable secure digital operations across all departments.
We offer endpoint protection, network security, cloud security, vulnerability assessments, penetration testing, identity and access management (IAM), compliance tools, and AI-powered threat detection systems tailored to your needs.
A robust cybersecurity system typically includes intrusion detection and prevention, real-time threat alerts, role-based access controls, encryption, audit logging, multi-factor authentication, and automated response workflows.
Development time depends on the complexity and scope — simple modules can take 2–4 weeks, while comprehensive enterprise-grade solutions may require 2–4 months, including testing, deployment, and training.
Yes, we support seamless integrations with cloud platforms, SIEM tools, DevOps pipelines, and business apps like payment gateways, CRMs, and productivity suites to secure your entire ecosystem.
Our solutions undergo rigorous testing, compliance checks, and real-world simulations. We follow best practices in secure coding, encryption standards, and regular vulnerability assessments.
Absolutely. Our solutions are designed to scale, capable of monitoring and protecting millions of requests per day without compromising performance or user experience.
We offer continuous monitoring, incident response assistance, regular patching, and a dedicated security support team to assist with alerts, updates, and evolving security needs.
Yes. We analyze your threat landscape, business operations, and compliance needs to develop tailored solutions that align precisely with your risk profile and technical infrastructure.
 Contact Us
Contact UsAccelerate Your Business with LasyaAitech


Partner with our expert software development team to bring your vision to life. Delivering innovative solutions and ensuring your project’s success every step of the way!
What are the key benefits of partnering with LasyaAitech?
We provide end-to-end software development services, from initial concept to deployment. Whether it's web development, mobile apps, or integrating cutting-edge technologies like AI, our solutions are tailored to your unique business needs, ensuring high performance, scalability, and exceptional user experiences.
How does your software development process work?
We follow a structured approach, starting with an in-depth consultation to understand your requirements. Our team then drafts a clear project roadmap, ensuring transparency and regular updates throughout development. From prototyping to testing and deployment, we work collaboratively to bring your vision to life.
Can LasyaAitech help us scale our existing software or migrate to new technology?
Absolutely! We specialize in upgrading existing systems, improving performance, and enabling seamless migration to modern technologies. Our team ensures minimal downtime and a smooth transition tailored to your growth objectives.
Why should I choose LasyaAitech over other software development companies?
With a proven track record of delivering successful projects like MailBluster and ThemeWagon, we combine technical expertise with a client-first approach. Our agile methods and attention to detail ensure we exceed expectations and deliver measurable results.
How do you ensure the security and scalability of your solutions?
We prioritize security at every stage of development, implementing industry-best practices to protect your data and systems. Our solutions are designed to be scalable, allowing your business to grow without limitations, ensuring long-term success.